
vgws
👋 WELCOME to Phish & Tell™️, from Security Done Easy™️
You’re not just building a business.
You’re building something worth protecting.

Also, my weekly one single focused tip on Wednesdays starts next week. (You’ll be able to opt out without unsubscribing from everything.) Stay tuned!
🎣 TOP CYBERSECURITY NEWS STORIES OF THE WEEK
Top stories of the week, how they are relevant to you, and what to do about them.
WordPress sites hijacked to hide malware
Source: Hackers Abuse Blockchain Smart Contracts to Spread Malware via Infected WordPress Sites, The Hacker News
What happened: Security researchers reported that a criminal group is hijacking poorly‑maintained WordPress sites to deliver infostealer malware. Hackers use a technique called “EtherHiding,” storing malicious JavaScript in Ethereum smart contracts and then loading that code onto compromised WordPress themes and plugins. The hidden code delivers stealers to visitors.
Why it matters: Many businesses use WordPress. Attackers look for outdated themes or plugins to inject malicious code. Once a site is compromised, visitors can be infected, the business’s reputation can be damaged, and sensitive customer data may be at risk.
What you can do: Keep your WordPress core, themes and plugins up to date. Remove any unused plugins and only install trusted ones. Monitor your site files for unexpected changes and consider using a Web Application Firewall (WAF) and malware‑scanning plugin to catch injected scripts. (We have a free guide to securing your WordPress site here.)
Misconfigured Invoicely database exposes customer data
Source: Nearly 180K Invoicely records left exposed online, SC World
What happened: Cybersecurity researcher Jeremiah Fowler discovered a publicly accessible database tied to the invoicing platform Invoicely that held 178,519 files. The misconfigured database contained banking information (PDFs and CSVs), invoices, scanned checks, tax documents, and personal details such as names, tax IDs, phone numbers and addresses. It remains unclear whether the database was operated by Invoicely or a third‑party contractor, how long it was exposed, or whether it was accessed by criminals. The database was taken offline after Fowler reported it; he noted that encryption should protect data even when repositories are inadvertently exposed.
Why it matters: Small businesses often use online invoicing services to streamline billing. Exposed financial and personally identifiable information can enable invoice fraud, identity theft and targeted phishing. Even if the leak has been secured, the data may have been copied.
What you can do: If you use Invoicely or similar services, check for breach notifications and monitor accounts for unusual activity. Contact your provider to confirm whether your data was involved and ensure they encrypt sensitive files. Avoid sending unprotected financial documents via email or public links, and implement multi‑factor authentication on invoicing accounts to reduce the risk of unauthorized access.
Phishing emails impersonate password‑manager breaches
Source: Fake LastPass, Bitwarden breach alerts lead to PC hijacks, Bleeping Computer
What happened: BleepingComputer reports that threat actors are sending fake breach‑notification emails to LastPass and Bitwarden users. The messages claim the password‑manager services were hacked and urge recipients to download an “improved” desktop app. The supplied installer actually deploys a remote‑monitoring tool, which in turn drops an app to give attackers remote access to the victim’s PC.
Why it matters: Small‑business owners often use password managers to protect accounts across multiple services. Falling for these phishing emails could hand attackers remote control of a company computer, allowing them to steal credentials, install malware, disable security software and siphon sensitive data. The campaign’s sophistication—using legitimate remote‑management tools and urgent breach claims—makes it more likely that busy staff could be tricked.
What you can do: Treat unsolicited security alerts with skepticism. If you receive an email claiming LastPass, Bitwarden or another service was breached, do not click embedded links or download attachments; instead, visit the official website or app directly to check for alerts. Verify sender addresses carefully. Enable multi‑factor authentication on password‑manager accounts and ensure endpoint protection is enabled. Educate employees, and remember that legitimate companies will never ask for your master password.
Not sure what applies to your business or what your options are? Let’s talk.
🔍 In Case You Missed It (ICYMI)
This week’s blog post: Cyber Incidents and Liability: What Every Small Business Owner Needs to Know » When a cyber incident happens (and they do happen), you can be held legally and financially responsible for the fallout.
🤖 The LOL-gorithm
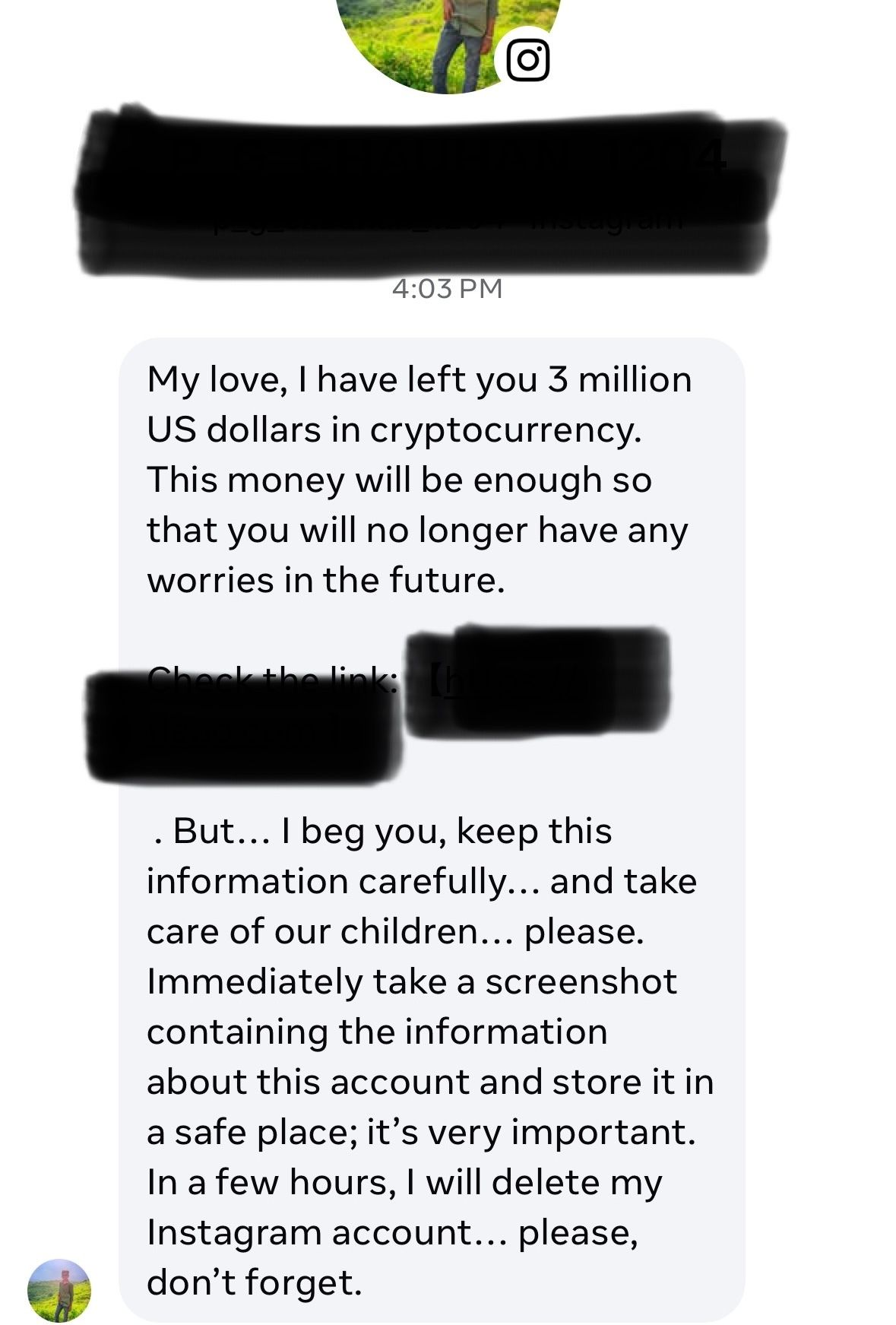
This week’s joke is not a cartoon or meme I found. It’s an actual direct message I got on Instagram. Most messages are more sophisticated now, so this one made me chuckle.
🧷 THE SAFETY SNAP
Don’t fall for fake security alerts
This week’s scam‑awareness reminder comes from a Malwarebytes report on a fake Robinhood security text. Victims receive a message claiming their account is locked and urging them to click a link or reply “Y.” The link leads to a realistic‑looking login page designed to steal your credentials. (I’ve gotten them from other finance-related apps, myself.)
What you should do:
Ignore and delete unsolicited texts or emails asking you to log in or confirm information. Real companies rarely ask you to reply “Y” to unlock an account.
Do not click links in messages; instead, go directly to the official website or app. Check that the domain is correct before entering credentials.
Enable two‑factor authentication, especially on financial and email accounts. This provides a second layer of protection even if your password is stolen.
Report the scam to the impersonated company so they can warn other customers, and consider forwarding the message to your cellular carrier’s spam reporting number. You’ll help keep someone else safe.
Stay vigilant: if something feels urgent, pause and verify through trusted channels.
💬 A PERSONAL NOTE
Have you ever taken photos with a camera that uses film, as opposed to a digital camera? Have you ever developed print photos in a darkroom? I met Emmanual at a Verizon Digital Ready small business “Ask the Expert” session this week. Emmanual runs swapfilm.co and is from San Fransisco. His love for film came right through the screen. If you are a photography lover, check his site out.
If you haven’t done a Verizon “ask the expert” session yet, please do, they are fantastic. My first one startled me because I expected a webinar and before I knew it, I was face to face with an expert and one other business owner and we were working on our competitive analysis. Verizon offers this free coaching and lots of other free classes on business topics from finance to marketing. (The sessions also help qualify you for their grants.)
👂 TELL ME
I’d love your feedback—do you like the new 3-story format? Just hit “reply” and let me know!
Stay safe and see you next week! 🌟

You’re subscribed to Phish & Tell™️ because your business is worth protecting.
🩷

